A couple of months ago I was working with a client doing some upgrades in their cloud infrastructure hosted in AWS, they were using Mode as data analytic platform, and since their database had public access at that moment they were doing the connection directly in Mode with their database.
As you know having an exposed public database is a big no no, mostly for security reasons, so part of the upgrade was to solve this issue, the migration of their public database to a internal network, so the database will have internal access only. If you ever crossed with a situation similar like this one, you’ll think that there is a couple of things we can, create a bastion host or vpn access so Mode can have access to the internal database.
The good news is that in our case this was not required since our friends of Mode provide us with an option to use a client that solve the connectivity issue between their service and the internal database. This mode’s bridge connector can be run as a container and since we already had a AWS Fargate cluster already configured we decided to run the mode’s bridge connector in it.
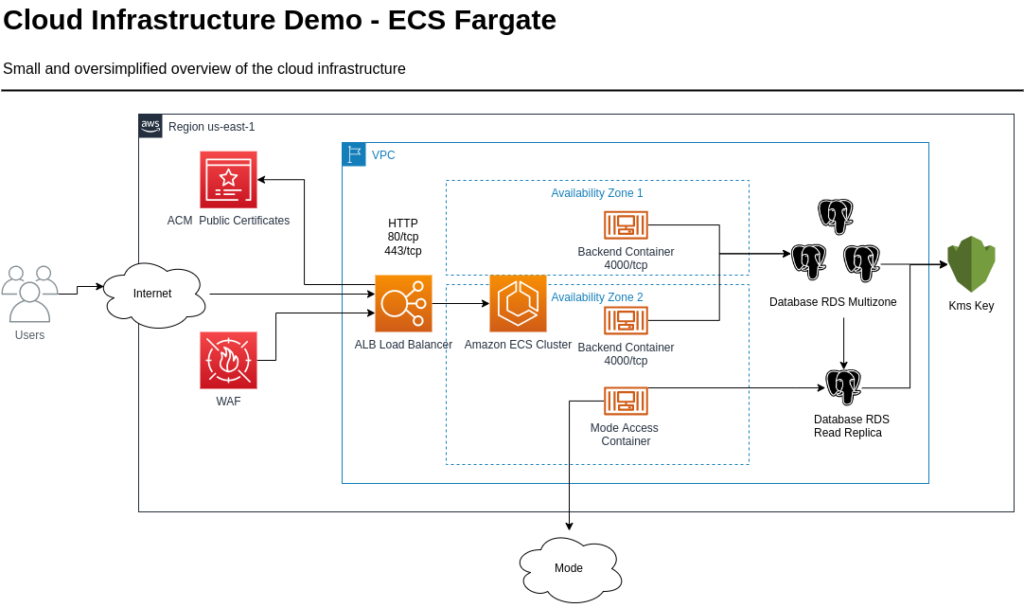
Let’s see the following image for more context of the cloud architecture hosted in AWS and how Mode bridge connector will be configured:
 `
`
We can see a small and oversimplified overview of the architecture, you can see an AWS ECS Fargate cluster and a Multizone database with a read replica configured in an internal network.
Since Mode’s bridge connector doesn’t need to listen any port and it connect directly to Mode service using internet we don’t need to add any extra security configuration.
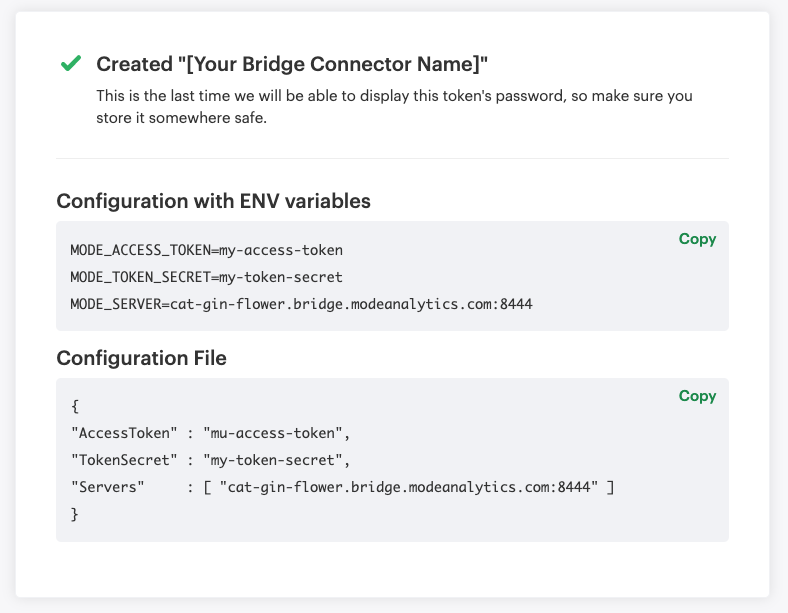
The only requirement we need is to create Mode’s bridge connector access tokens:
Create the task definition to execute the container, you can find the docker image in docker hub. The only security concern I had using an external docker image is that you depend of the security of a third party, it should be a better idea to create a internal AWS ECR repository adding a security scan for this image and use a read only replica database for queries.
In this example I added the access token as secret strings in SSM parameter store, these secrets will be injected in the container.
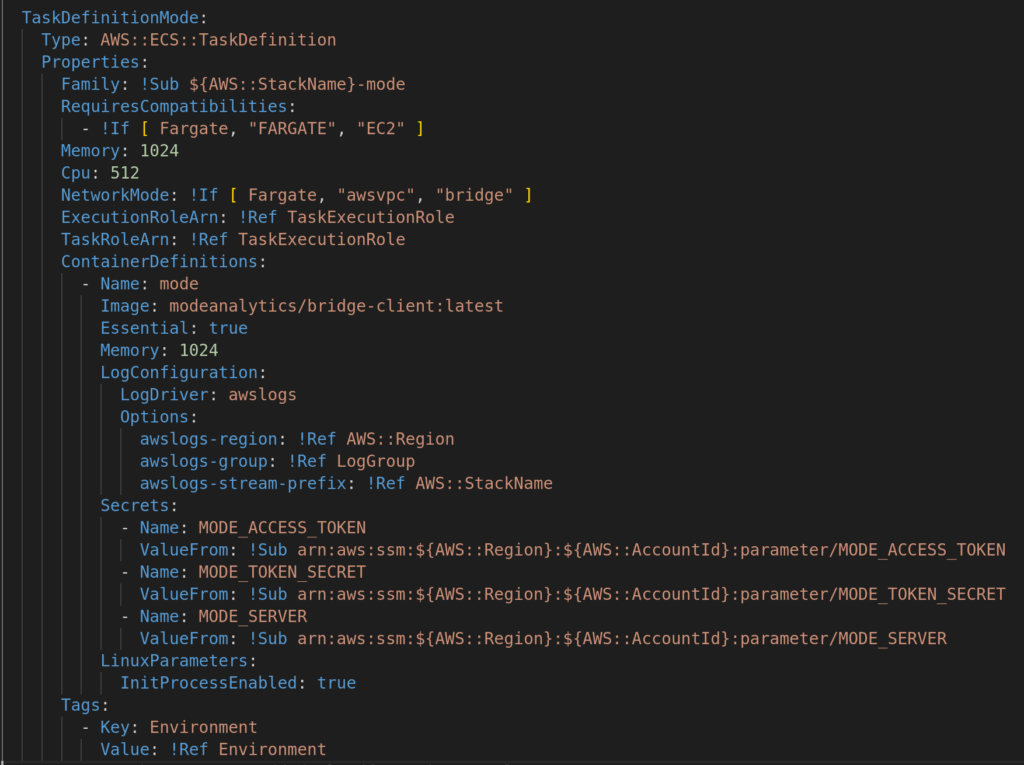
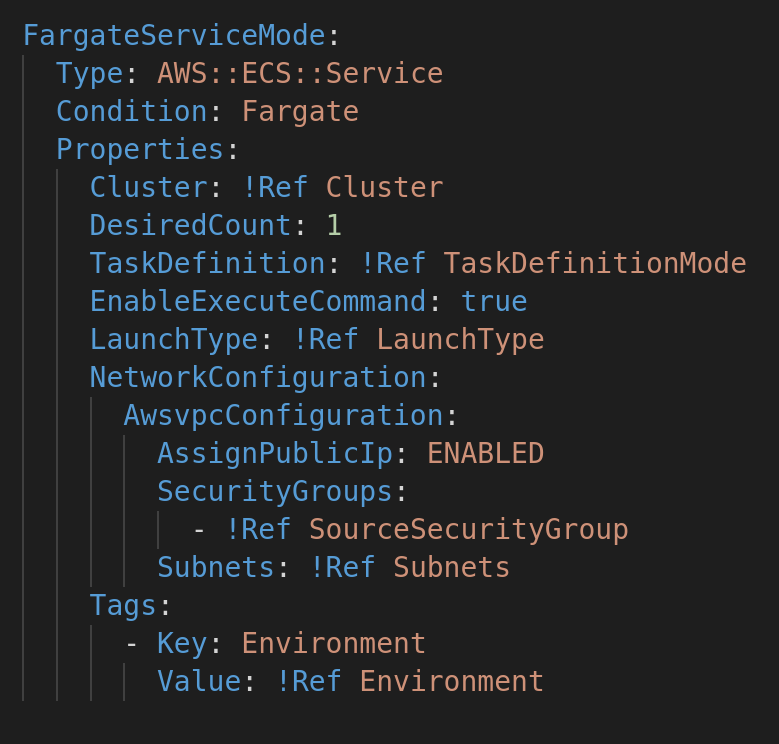
Create the fargate service and deploy it in the cluster:
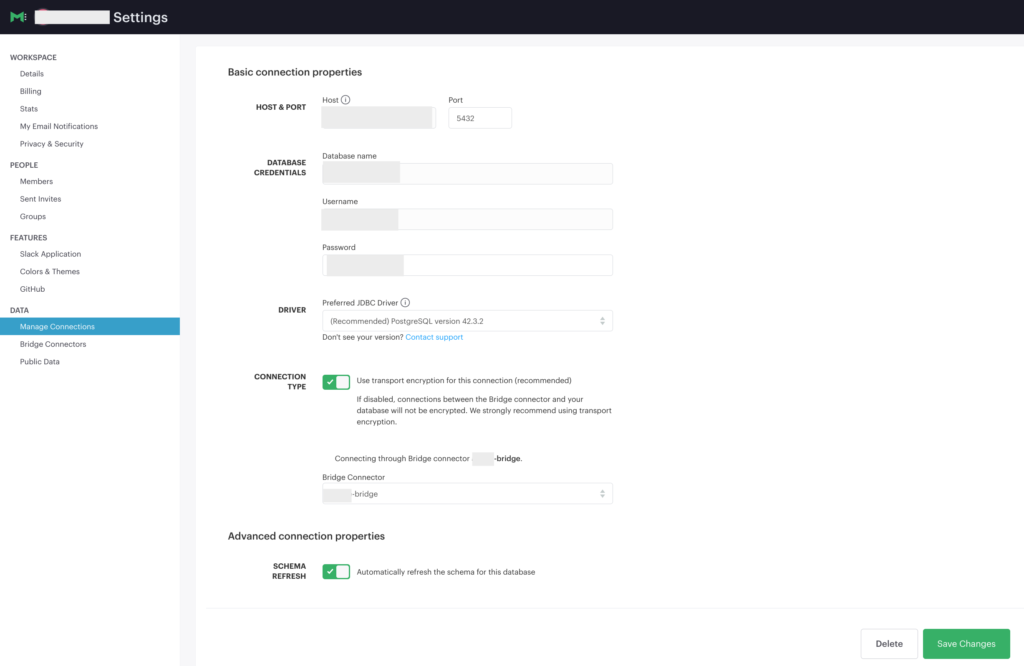
Once the bridge connector is running you can finish the configuration of the database connection in Mode:
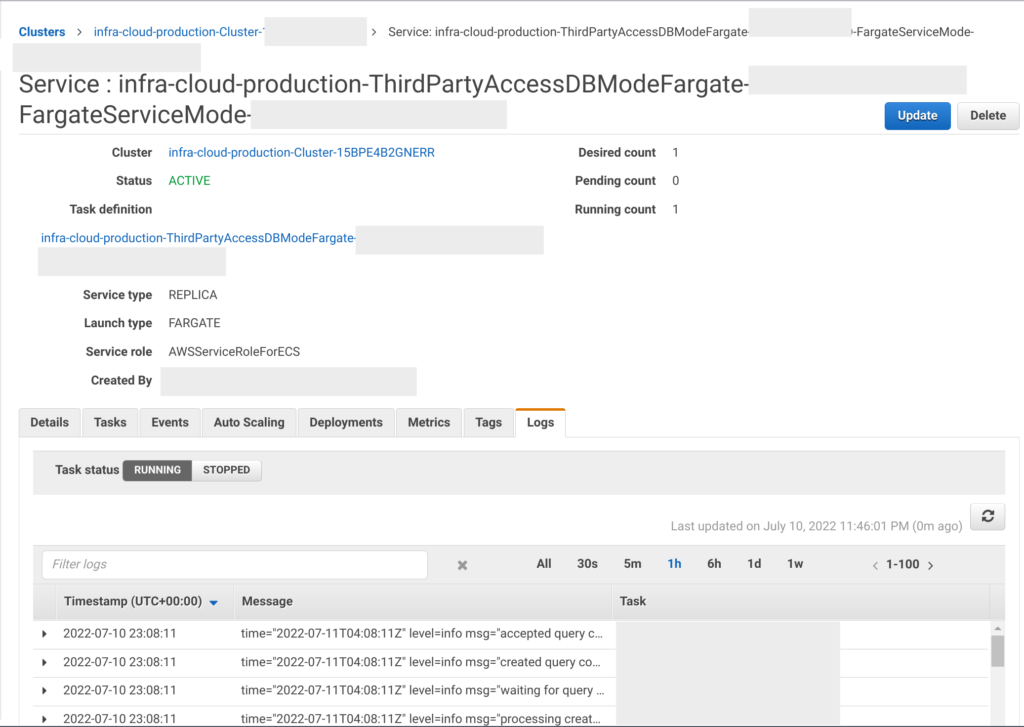
You can check the status of the connection in the logs of the container in the AWS Fargate cluster:
You can find an example of the configuration I used with cloudformation in this github repository