A network security group is a set of rules that are used to allow or block network traffic in a computer network. These groups are often used to protect the network from external attacks or to limit access to certain network resources to only certain users or devices.
In Microsoft Azure, you can use an Azure network security group to filter network traffic between Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
You can deploy resources from several Azure services into an Azure virtual network. For a complete list, see Services that can be deployed into a virtual network. You can associate zero, or one, network security group to each virtual network subnet and network interface in a virtual machine. The same network security group can be associated to as many subnets and network interfaces as you choose.
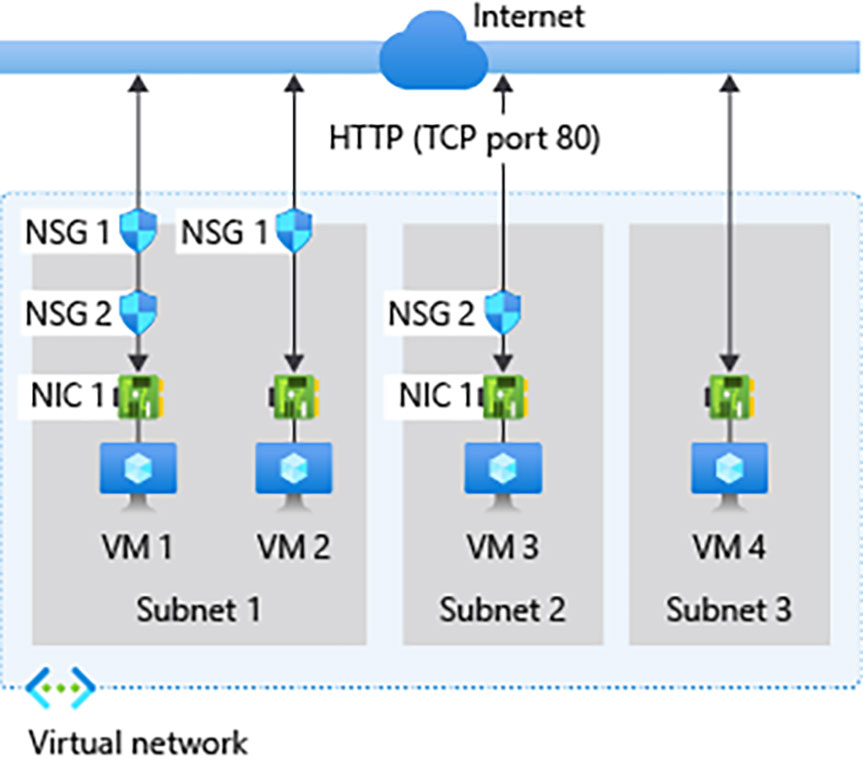
For example: the following picture illustrates different scenarios for how network security groups might be deployed to allow network traffic to and from the internet over TCP port 80:
Security rules
A network security group contains zero, or as many rules as desired, within Azure subscription limits. Each rule specifies the following properties:
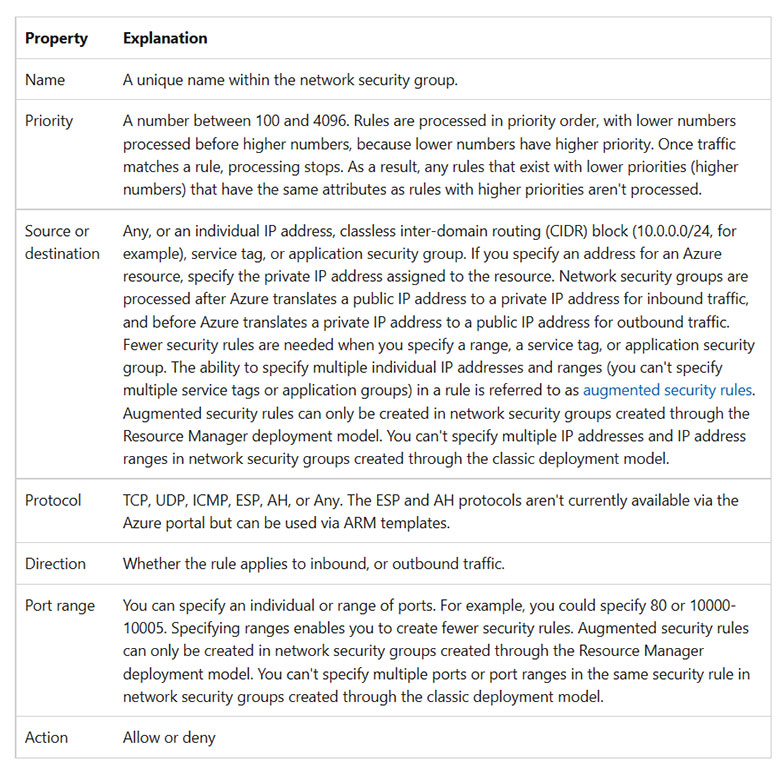
Security rules are evaluated and applied based on the five-tuple (source, source port, destination, destination port, and protocol) information. You can’t create two security rules with the same priority and direction.
A flow record is created for existing connections. Communication is allowed or denied based on the connection state of the flow record. The flow record allows a network security group to be stateful. If you specify an outbound security rule to any address over port 80, for example, it’s not necessary to specify an inbound security rule for the response to the outbound traffic. You only need to specify an inbound security rule if communication is initiated externally. The opposite is also true. If inbound traffic is allowed over a port, it’s not necessary to specify an outbound security rule to respond to traffic over the port.
If you want to know more about network security group please visit the follow link
Deploy Network Security Group with Terraform in 2 min
Lets create a demo to deploy a Network Security Group using Terraform in Azure, we can do it quickly with the support of the hashicorp documentation,
Prerequisites:
- Azure Account, If you don’t have an Azure subscription, create a free account before you begin.
- Configure Terraform: If you haven’t already done so, configure Terraform using one of the following options.
Step 1 – Clone the following repository and open it with Visual Studio Code,
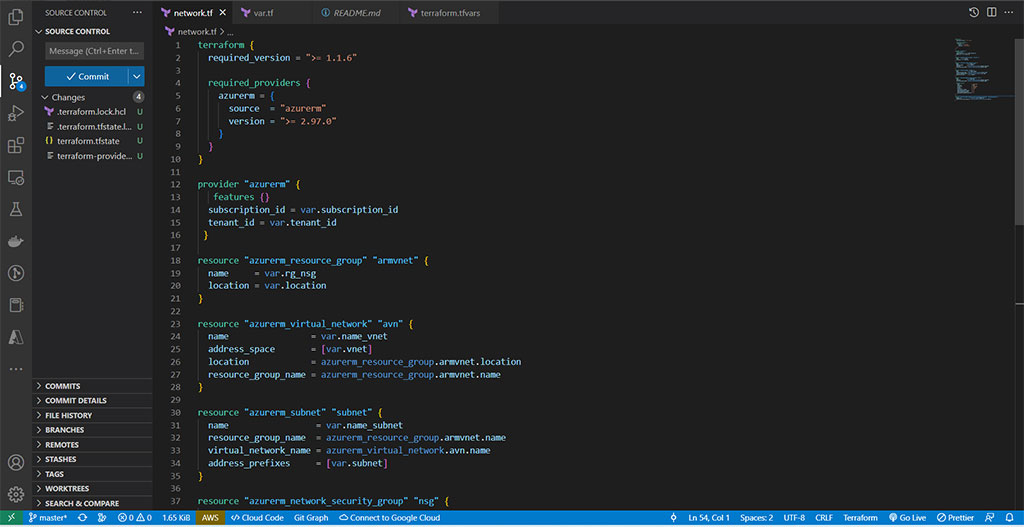
In the terraform.tfvars file, change variables and settings.
#Information tenant and subscription
subscription_id = "3566sdds-54fd-7458-7d8d-s45da96w24e2"
tenant_id = "ah582g46-bg58-3ed8-sd65-sfsd89985ds2"
rg_nsg = "RG-NSG"
location = "eastus"
vnet = "10.0.0.0/16"
name_vnet = "VNET"
subnet = "10.0.2.0/24"
name_subnet = "SUBNET"
name_nsg = "NSG"Step 2 – Open the CLI and start terraform with the next command.
terraform init
terraform validate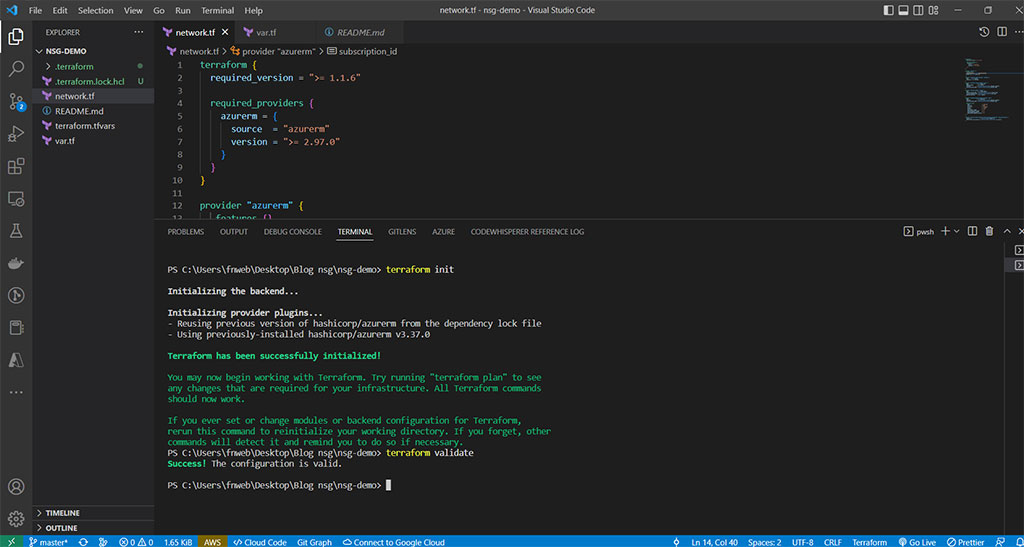
Our next step is to execute the plan command.
terraform plan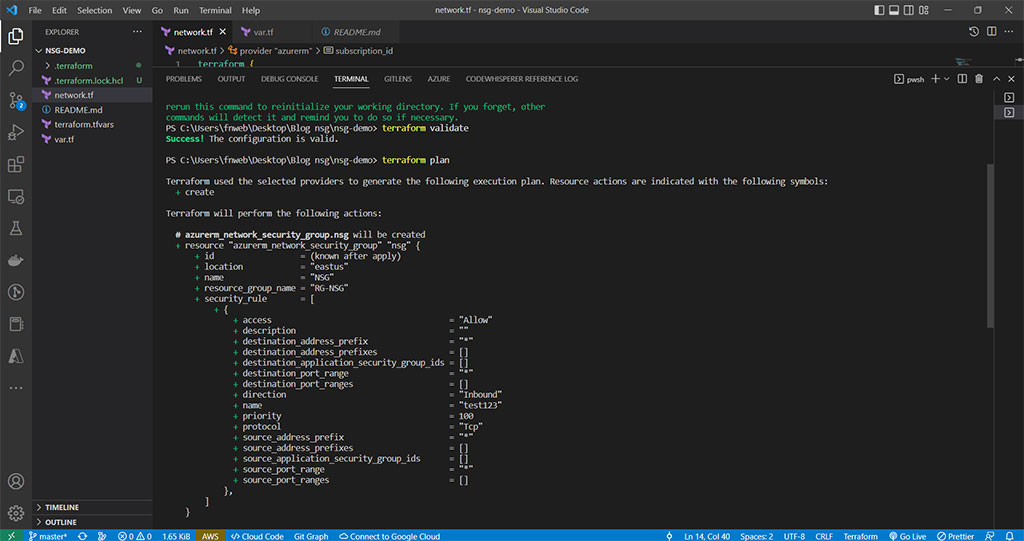
We continue and deploy the changes.
terraform apply -auto-approve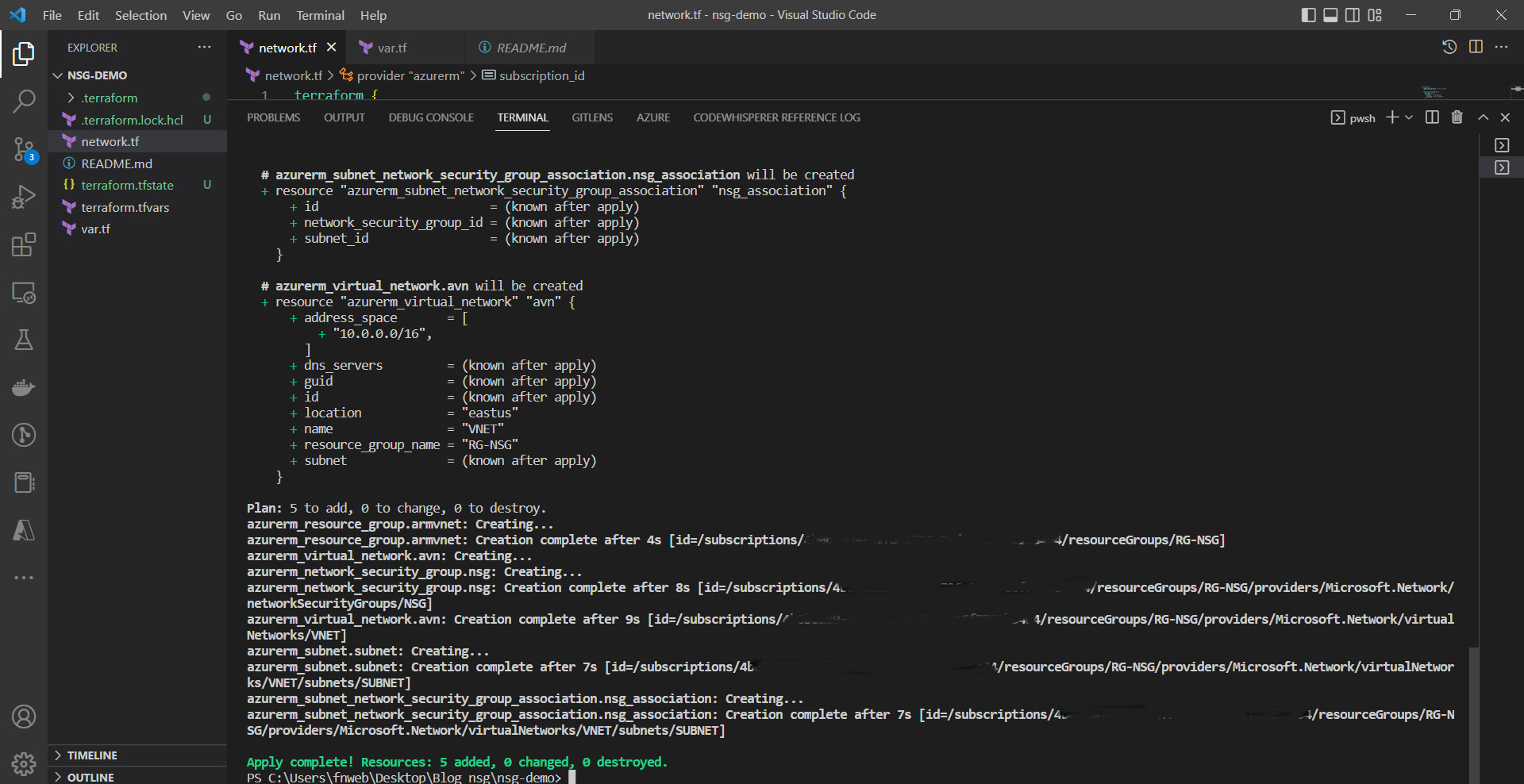
Step 3 – Go to the Azure portal and check if everything is ok
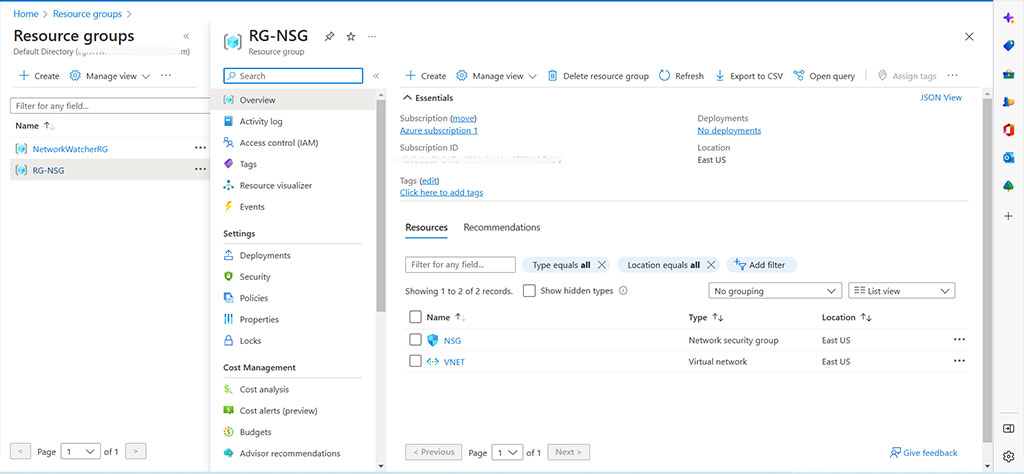
Congratulations, here concludes our demo. We can delete our network security group resource with the following command:
terraform destroy -auto-approveContact us for more information or visit our blog.